Using TCP Wrapper to help secure OpenSSH
This is part of a series on hosting a website on the Raspberry Pi. Click the Raspberry Pi Webserver in the Blog Series to the right for the complete steps.
To use TCP Wrapper, the given executable/service must be compiled with TCP Wrappers. Lets test OpenSSH to see if it is indeed compiled with TCP Wrapper.
First, find the location of the SSHD program on your computer using the whereis command.
whereis sshd
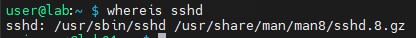
With the location of SSHD found, we use ldd command to see if libwrap.so (TCP Wrapper library) is a dependency. Grepping for the library makes it a little easier to see that it is compiled with the TCP Wrapper library.
ldd /usr/sbin/sshd | grep libwrap.so
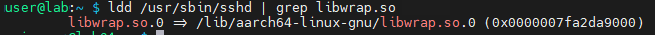
As you can see, it is indeed compiled with the TCP Wrapper library. Lets configure the TCP Wrapper to limit access to OpenSSH.
To only allow a SSH connections from my local network, we will deny all hosts trying to connect to it and allow only IP addresses from the local network.
Enter this command to edit hosts.deny file.
sudo nano /etc/hosts.deny
Add the following line to deny all host trying to connect.
sshd: All
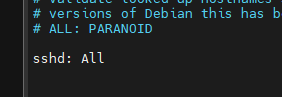
Save and close the file.
Use this command to edit hosts.allow file.
sudo nano /etc/hosts.allow
Add the follow line to only allow connections from the local network or you could just as well specify a single IP address and remove the /24 to allow just one computer access.
sshd: 192.168.2.0/24
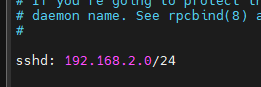
Save and close the file.
There are no restart to perform, so go ahead and test the system. You should only have access from the local network or single machine, depending on how you configured it.
Check our the next post in this series to continue: Install Uncomplicated Firewall – UFW
Share this content:
Leave a Reply