Modifying the config file of OpenSSH to help secure it.
This is part of a series on hosting a website on the Raspberry Pi. Click the Raspberry Pi Webserver in the Blog Series to the right for the complete steps.
Start MobaXterm and connect to the Raspberry Pi.
Always make a backup of your config files before making changes to them.
Let’s start with adding a ssh-users group, and only users in this group will be able to login.
sudo groupadd ssh-users sudo usermod -aG ssh-users user
Moving to the config file location for OpenSSH, make a copy, and begin editing it.
cd /etc/ssh sudo cp sshd_config sshd_config_orig sudo nano sshd_config
I began by commenting out all active lines in the config file. Then copying the list (below table) and pasting it into the config file. All other entries are set to default by OpenSSH.
| Include /etc/ssh/sshd_config.d/*.conf | Add the other config files. |
| AcceptEnv LANG LC_* | Allow client to pass locale environment variables. |
| AddressFamily inet | Use IPv4 only. |
| AllowTcpForwarding no | No TCP forwarding. |
| AllowGroups ssh-users | The users from this group can log on. |
| AuthenticationMethods publickey | Only allow publickey logins. |
| ClientAliveCountMax 2 | After 2 ClientAliveInterval(below) of 15 seconds with no response, it will terminate the connection |
| ClientAliveInterval 15 | After a timeout interval of 15 seconds, if no data has been received from the client, it requests a response. |
| DenyUsers root | Root is not allowed to login. |
| KbdInteractiveAuthentication no | No keyboard-interactive authentication. |
| LoginGraceTime 15 | 15 seconds to login. |
| LogLevel VERBOSE | Possible values are QUIET, FATAL, ERROR, INFO, VERBOSE, DEBUG, DEBUG1, DEBUG2, and DEBUG3. |
| MaxAuthTries 1 | Only give one try to login. |
| PasswordAuthentication no | No password authentication |
| PermitRootLogin no | Do not allow the root to login. |
| Port 2222 | Change the port to help stop some of the bots that just attack port 22. You can pick any port number that is not in use. |
| PrintMotd no | Don’t print file /etc/motd after user logs in interactively. |
| Subsystem sftp /usr/lib/openssh/sftp-server | Override default of no subsystems. |
| UsePAM no | No PAM accounts |
Include /etc/ssh/sshd_config.d/*.conf AcceptEnv LANG LC_* AddressFamily inet AllowTcpForwarding no AllowGroups ssh-users AuthenticationMethods publickey ClientAliveCountMax 2 ClientAliveInterval 15 DenyUsers root KbdInteractiveAuthentication no LoginGraceTime 15 LogLevel VERBOSE MaxAuthTries 1 PasswordAuthentication no PermitRootLogin no Port 2222 PrintMotd no Subsystem sftp /usr/lib/openssh/sftp-server UsePAM no
After pasting the contents and making any changes to fine tune it, close the file and restart the SSH service using the command below.
sudo systemctl restart ssh
In MobaXterm, right click your session and select Edit session. In the popup window, on the far right change the Port number to the number you selected. With the example above the Port number is 2222.
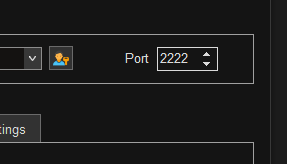
Click OK to close the window. Double clicking your session will open a new tab and connect to the Raspberry Pi using the new configuration.
With OpenSSH a lot more secure, check our the next post in this series to continue: Using TCP Wrapper to help secure OpenSSH
Share this content:
Leave a Reply